4. Architecture
aevatar.ai comprises three primary components:
- aevatar Framework
- aevatar Station
- aevatar Agents
They synergies to manage the entire lifecycle of multiple AI agents—from creation to deployment and ongoing operation.
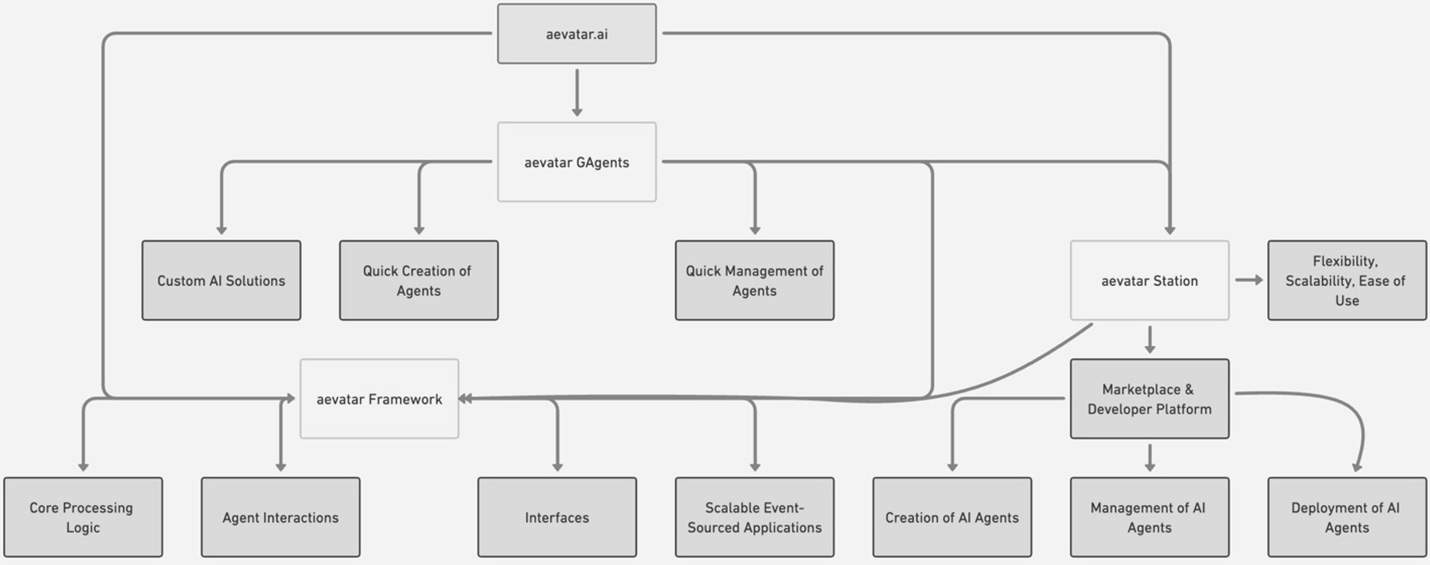
4.1 aevatar Framework
aevatar Framework is designed to support AI agents and event sourcing mechanisms, providing a modular architecture for extensibility and maintainability. It leverages design patterns such as Dependency Injection and Observer Pattern to enhance flexibility and scalability.

Design Principles
- Modularity: The framework is designed to be modular, allowing developers to add or remove components as needed.
- Extensibility: New features can be added through plugins without altering the core framework.
- Separation of Concerns: Each component has a specific responsibility, promoting maintainability and readability.
The framework provides a flexible architecture for developing AI agents and event sourcing applications, allowing for easy integration and extension through its modular design. By adhering to design principles and patterns, the framework ensures that it remains scalable and maintainable as new features are added.
4.2 Core Components Overview
Actor Model
- Responsible for managing distributed actor (Grain) lifecycle and communication, providing a stateful and replayable execution environment for each agent, ensuring high concurrency and scalability for the system.
GAgent
- Each submodule (such as Telegram, Twitter, MicroAI, SocialAgent, etc.) is an independent GAgent, implementing specific agent logic for different platforms or scenarios, supporting cross-platform expansion.
Event Sourcing
- Provides core functionality for log storage, event replay, and snapshot management. This supports multiple backend storage options like MongoDB and Redis, and ensures system traceability and audit capabilities.
- All critical agent events (i.e. received messages, state updates, model inference outputs) can be persisted, providing replay and audit capabilities.
CQRS (Command Query Responsibility Segregation)
- Externally provides REST/gRPC interfaces and supports efficient internal data querying and indexing through read-write separation architecture. Combined with solutions like Elasticsearch, it enables fast retrieval of large-scale data.
- Read-write separation: The system can handle agent state change write requests (events) independently from external query interfaces.
- Combined with Elasticsearch/MongoDB for rapid retrieval and multi-dimensional queries.
aevatar Dashboard
- Graphical management tool allowing users to configure multi-agent collaboration processes, monitor event flows, and edit business logic through low-code/no-code approaches. This significantly reduces development barriers, especially for non-technical users.
4.3 GAgent Multi-Agent Collaboration Model
- Adopts
GAgentBase<TState, TEvent>as an abstract base class, where agents can inherit and implement their own business processing methods.
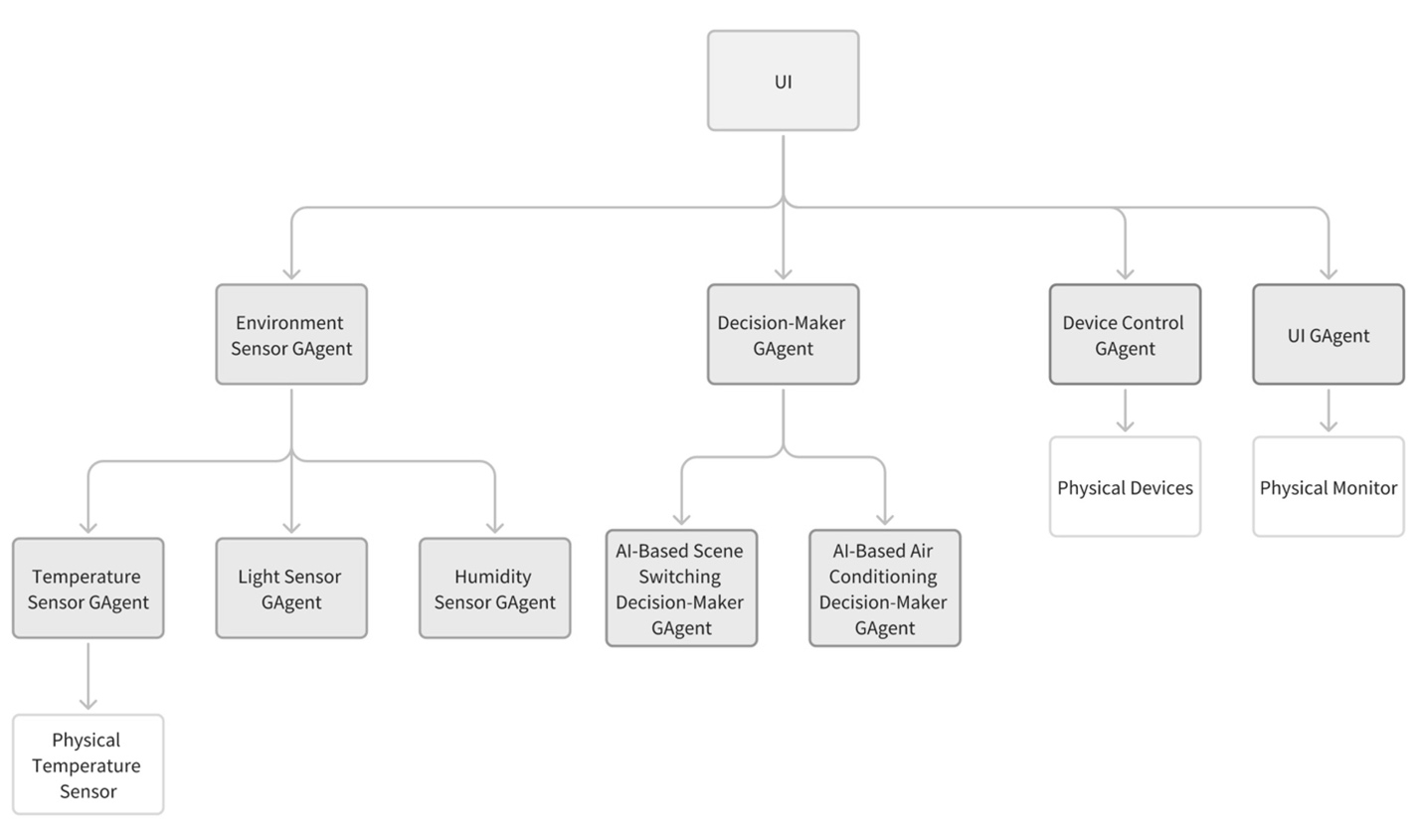
- GAgent: Manages subscription, message routing, and event coordination for multiple agents within a group, enabling broadcast, point-to-point, or tree-based event transmission within the group.
4.4 Multi LLMs Orchestration
- Multi-Pronged Approach: Incorporates access to multiple LLMs (GPT-4, Claude, Llama2, etc.) through 'AIService' and Semantic Kernel mechanisms.
- Scheduling Strategy: Dynamically decides which model(s) to call based on task type, resource cost, complexity, and other dimensions.
- Model Adaptation Layer: Connect to more third-party or private models at the framework level, providing enterprises with customised multi-language model management.
4.5 Cloud-Native Deployment and Security Compliance
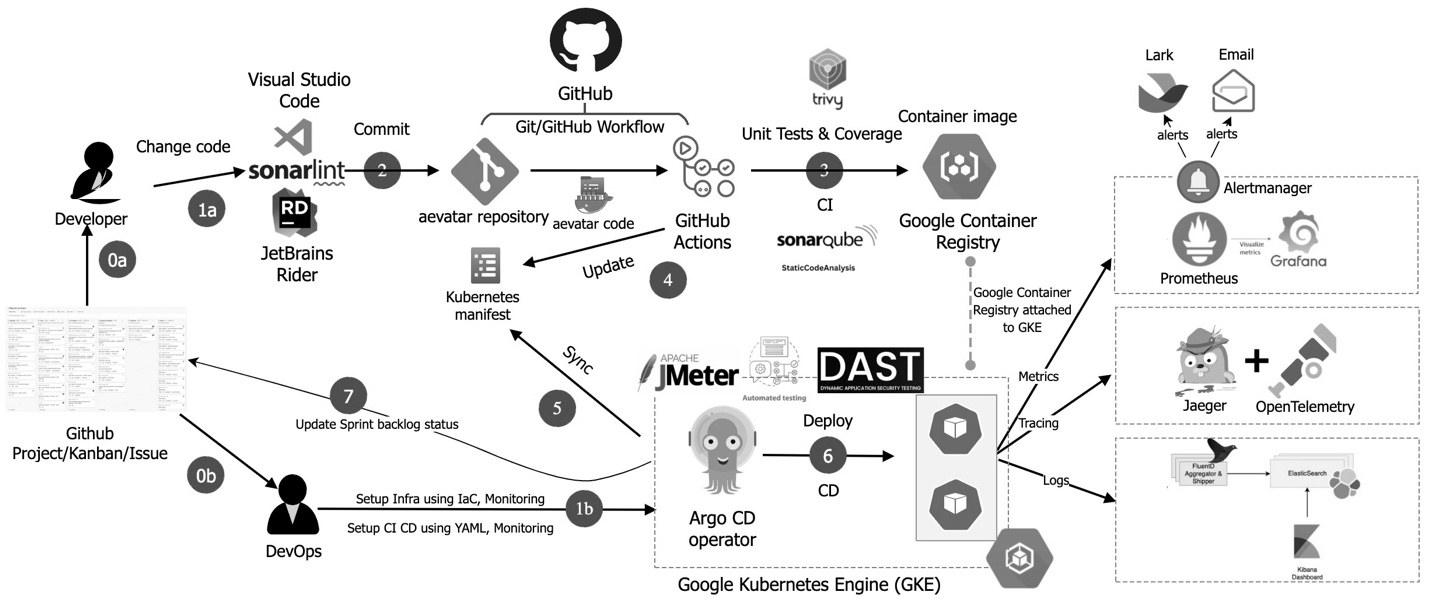
Kubernetes Deployment
- Orleans Silo and agent services can be containerised, supporting automatic scaling (HPA), service discovery, and elastic load balancing.
DevSecOps & GitOps
- Provides container image security scanning, CI/CD integration, and Infrastructure as Code (IaC) deployment, ensuring application security and traceability.
Security Policies
- Authentication through AuthServer and OAuth/OpenID systems, supporting multi- tenancy and RBAC (Role-Based Access Control).